TCP / IP
Definition: Transmission Control Protocol (TCP) and Internet Protocol (IP) are two distinct network protocols, technically speaking. TCP and IP are so commonly used together, however, that TCP/IP has become standard terminology to refer to either or both of the protocols.
IP corresponds to the Network layer (Layer 3) in the OSI model, whereas TCP corresponds to the Transport layer (Layer 4) in OSI. In other words, the term TCP/IP refers to network communications where the TCP transport is used to deliver data across IP networks.
The average person on the Internet works in a predominately TCP/IP environment. Web browsers, for example, use TCP/IP to communicate with Web servers.
used to connect hosts on the Internet. TCP/IP uses severalprotocols, the two main ones being TCP and IP. TCP/IP is built into the UNIX operating system and is used by the Internet, making it the de facto standard for transmitting data over networks. Evennetwork operating systems that have their own protocols, such asNetware, also supportTCP/IP.
Resource usage
Most implementations allocate an entry in a table that maps a session to a running operating system process. Because TCP packets do not include a session identifier, both endpoints identify the session using the client's address and port. Whenever a packet is received, the TCP implementation must perform a lookup on this table to find the destination process. Each entry in the table is known as a Transmission Control Block or TCB. It contains information about the endpoints (IP and port), status of the connection, running data about the packets that are being exchanged and buffers for sending and receiving data.
The number of sessions in the server side is limited only by memory and can grow as new connections arrive, but the client must allocate a random port before sending the first SYN to the server. This port remains allocated during the whole conversation, and effectively limits the number of outgoing connections from each of the client's IP addresses. If an application fails to properly close unrequired connections, a client can run out of resources and become unable to establish new TCP connections, even from other applications.
Both endpoints must also allocate space for unacknowledged packets and received (but unread) data.
Data transfer
There are a few key features that set TCP apart from User Datagram Protocol:
- Ordered data transfer — the destination host rearranges according to sequence number
- Retransmission of lost packets — any cumulative stream not acknowledged is retransmitted
- Error-free data transfer
- Flow control — limits the rate a sender transfers data to guarantee reliable delivery. The receiver continually hints the sender on how much data can be received (controlled by the sliding window). When the receiving host's buffer fills, the next acknowledgment contains a 0 in the window size, to stop transfer and allow the data in the buffer to be processed.
- Congestion control
Reliable transmission
TCP uses a sequence number to identify each byte of data. The sequence number identifies the order of the bytes sent from each computer so that the data can be reconstructed in order, regardless of any fragmentation, disordering, or packet loss that may occur during transmission. For every payload byte transmitted, the sequence number must be incremented. In the first two steps of the 3-way handshake, both computers exchange an initial sequence number (ISN). This number can be arbitrary, and should in fact be unpredictable to defend against TCP sequence prediction attacks.
TCP primarily uses a cumulative acknowledgment scheme, where the receiver sends an acknowledgment signifying that the receiver has received all data preceding the acknowledged sequence number. The sender sets the sequence number field to the sequence number of the first payload byte in the segment's data field, and the receiver sends an acknowledgment specifying the sequence number of the next byte they expect to receive. For example, if a sending computer sends a packet containing four payload bytes with a sequence number field of 100, then the sequence numbers of the four payload bytes are 100, 101, 102 and 103. When this packet arrives at the receiving computer, it would send back an acknowledgment number of 104 since that is the sequence number of the next byte it expects to receive in the next packet.
Also Known As: Transmission Control Protocol / Internet Protocol
WAN TECHNOLOGY
WANs are all about exchanging information across wide geographic areas. They are also, as you can probably gather from reading about the Internet, about scalability—the ability to grow to accommodate the number of users on the network, as well as to accommodate the demands those users place on network facilities. Although the nature of a WAN—a network reliant on communications for covering sometimes vast distances—generally dictates slower throughput, longer delays, and a greater number of errors than typically occur on a LAN, a WAN is also the fastest, most effective means of transferring computer-based information currently available.
Circuit Switching
Circuit switching involves creating a direct physical connection between sender and receiver, a connection that lasts as long as the two parties need to communicate. In order for this to happen, of course, the connection must be set up before any communication can occur. Once the connection is made, however, the sender and receiver can count on "owning" the bandwidth allotted to them for as long as they remain connected.
Although both the sender and receiver must abide by the same data transfer speed, circuit switching does allow for a fixed (and rapid) rate of transmission. The primary drawback to circuit switching is the fact that any unused bandwidth remains exactly that: unused. Because the connection is reserved only for the two communicating parties, that unused bandwidth cannot be "borrowed" for any other transmission.
The most common form of circuit switching happens in that most familiar of networks, the telephone system, but circuit switching is also used in some networks. Currently available ISDN lines, also known as narrowband ISDN, and the form of T1 known as switched T1 are both examples of circuit-switched communications technologies.
Message Switching
Unlike circuit switching, message switching does not involve a direct physical connection between sender and receiver. When a network relies on message switching, the sender can fire off a transmission—after addressing it appropriately—whenever it wants. That message is then routed through intermediate stations or, possibly, to a central network computer. Along the way, each intermediary accepts the entire message, scrutinizes the address, and then forwards the message to the next party, which can be another intermediary or the destination node.
What's especially notable about message-switching networks, and indeed happens to be one of their defining features, is that the intermediaries aren't required to forward messages immediately. Instead, they can hold messages before sending them on to their next destination. This is one of the advantages of message switching. Because the intermediate stations can wait for an opportunity to transmit, the network can avoid, or at least reduce, heavy traffic periods, and it has some control over the efficient use of communication lines.
Examples ofWide Area Network Technologies
Virtual private network (VPN) is a tecnology widely used in a public switched network (PSTN) to provide private and secured WAN for an organization. VPN uses encryption and other techniques to make it appear that the organisation has a dedicated network, while making use of the shared infrastructure of the WAN.
WAN technologies generally function at the lower three layers of the OSI reference model: the physical layer, the data link layer, and the network layer. Key technologies often found in WANs include SONET, Frame Relay, X.25, ATM and PPP.
- ATM: A dedicated-connection switching technology that organizes digital data into 53-byte cell units. Individually, a cell is processed asynchronously relative to other related cells and is queued before being multiplexed over the transmission path. Speeds on ATM networks can reach 10 Gbps.
- Frame Relay: (FR). A high-speed packet-switched data communications service, similar to X.25. Frame relay is widely used for LAN-to-LAN interconnect services, and is well suited to the bursty demands of LAN environments.
- SONET/SDH: Synchronous Optical Network is an international standard for high speed communication over fiber-optic networks. The SONET establishes Optical Carrier (OC) levels from 51.8 Mbps to 10 Gbps (OC-192) or even higher. Synchronous Digital Hierarchy (SDH) is a European equivalent of SONET.
- X.25: The X.25 protocol allows computers on different public networks to communicate through an intermediary computer at the network layer level.
- PPP: A point-to-point link provides a single, pre-established WAN communications path from the customer premises through a carrier network, such as a telephone company, to a remote network. Point-to-point lines are usually leased from a carrier and thus are often called leased lines. For a point-to-point line, the carrier allocates pairs of wire and facility hardware to your line only.
IP can also be considered as a WAN technology in the packet switching environment.
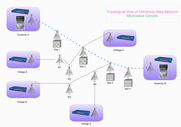
Symbols of Network Architecture
Some network mapping symbols for network engineer. Provide a Common Graphics Technology for Network Mapping.
DNS
The Domain Name System (DNS) is a hierarchical distributed naming system for computers, services, or any resource connected to the Internet or a private network. It associates various information with domain names assigned to each of the participating entities. Most prominently, it translates easily memorizeddomain names to the numerical IP addresses needed for the purpose of locating computer services and devices worldwide. The Domain Name System is an essential component of the functionality of the Internet.
An often-used analogy to explain the Domain Name System is that it serves as the phone book for the Internet by translating human-friendly computer hostnamesinto IP addresses. For example, the domain name www.example.com translates to the addresses 93.184.216.119 (IPv4) and 2606:2800:220:6d:26bf:1447:1097:aa7 (IPv6). Unlike a phone book, the DNS can be quickly updated, allowing a service's location on the network to change without affecting the end users, who continue to use the same host name. Users take advantage of this when they use meaningful Uniform Resource Locators(URLs), and e-mail addresses without having to know how the computer actually locates the services.
The Domain Name System distributes the responsibility of assigning domain names and mapping those names to IP addresses by designating authoritative name servers for each domain. Authoritative name servers are assigned to be responsible for their supported domains, and may delegate authority over subdomains to other name servers. This mechanism provides distributed and fault tolerant service and was designed to avoid the need for a single central database.
The Domain Name System also specifies the technical functionality of this database service. It defines the DNS protocol, a detailed specification of the data structures and data communication exchanges used in DNS, as part of the Internet Protocol Suite.
The Internet maintains two principal namespaces, the domain name hierarchy and the Internet Protocol (IP) address spaces. The Domain Name System maintains the domain name hierarchy and provides translation services between it and the address spaces. Internet name servers and a communication protocol implement the Domain Name System. A DNS name server is a server that stores the DNS records for a domain name, such as address (A or AAAA) records, name server (NS) records, and mail exchanger (MX) records (see also list of DNS record types); a DNS name server responds with answers to queries against its database.
resources: http://compnetworking.about.com/cs/basictcpip/g/bldef_tcpip.htm , http://www.webopedia.com/TERM/T/TCP_IP.html , http://en.wikipedia.org/wiki/Transmission_Control_Protocol , http://technet.microsoft.com/en-us/library/bb962087.aspx , http://www.edrawsoft.com/Wide-Area-Network.php , http://en.wikipedia.org/wiki/Domain_Name_System